🔥 update 2021-05-24 - Added K8s based setup
The main idea of this playground is to provide an easy to use LDAP - Lightweight Directory Access Protocol server to simply play around with the technology.
The Apache Directory™ Project - We strive to increase LDAP awareness, comfort and adoption to bring forth what we call the Modern LDAP Renaissance.
Prerequisites
This playground requires a ready to use Docker Compose environment.
For the impatient...
Grab your copy of the playground datenkollektiv/ldap-playground...
run up.sh to build and up the environment.
Note: You'll need to prepare a keystore. Check the chapter Prepare a keystore below in case you need some guidance.
Your LDAP server is ready to go - check out the local server at ldap://localhost:389.
Deep dive - K8s based setup
- port
389exposed (the default LDAP port)
k3d cluster create \
--port 389:389@loadbalancer ldap
…
INFO[0025] Starting cluster ‘ldap’
…
Prepare the k8s environment…
k3d kubeconfig get ldap > kube_config_cluster.yml
export KUBECONFIG=$(PWD)/kube_config_cluster.yml
…and spin-up the application:
kubectl create configmap seed-data.ldif --from-file=docker/ldap/seed-data.ldif
kubectl apply -f k8s-openldap-statefulset.yml
kubectl apply -f k8s-ldap-loadbalancer.yml
kubectl apply -f k8s-ldap-ingress.yml
Check if we can access the LDAP server with ldapsearch:
ldapsearch -H ldap:// -b dc=datenkollektiv,dc=de -D "cn=admin,dc=datenkollektiv,dc=de" -w openldap
...
# search result
search: 2
result: 0 Success
# numResponses: 3
# numEntries: 2
🥳 Hooray!
CLI example with ldapmodify
Insert test data via ldapmodify until we figure out why the /seed approach didn’t work.
$ ldapmodify -H ldap:// -D "cn=admin,dc=datenkollektiv,dc=de" -w openldap -a -f docker/ldap/seed-data.ldif
adding new entry "ou=users,dc=datenkollektiv,dc=de"
adding new entry "cn=devop,ou=users,dc=datenkollektiv,dc=de"
adding new entry "cn=admin,ou=users,dc=datenkollektiv,dc=de"
Deep dive - Docker based setup
The main components you'll probably want to adapt and fine-tune your personal LDAP playground are:
- The Docker Compose configuration
docker-compose.yamland - the sample data
initial-import.ldif
Prepare a keystore
The setup requires a keystore to be present in docker/etc for TLS.
Note: use
changeitas password or updateAPACHEDS_TLS_KS_PWDindocker-compose.yamlaccordingly.
The keystore should be named apacheds.jks and can be generated like follows (You'll need the Java keytool):
keytool -genkeypair -alias apacheds -keyalg RSA -validity 7 -keystore apacheds.jks
Copy the generated keystore into the directory docker/etc
The configuration knobs
If unchanged the LDAP server will be available via ldap://127.0.0.1:389 or simply ldap:// and ldaps:// from the Docker host.
Check the port mappings in the docker-compose.yaml in case you don't want to use the default ports.
The initial data will be inserted from docker/data/initial-import.ldif.
So this is the natural place in case you want to fiddle with the initial data set.
First contact
Note: You can verify the installation from the host system with
ldapsearch -H ldap:// -x -s base -b "" -LLL "+"
CLI example with ldapmodify
ldapmodify -H ldap:// -D "uid=admin,ou=system" -w apacheds -a -f ldif-examples/users.ldif
Note: The preconfigured admin password is
apachedsand can be changed in thedocker-compose.yamlif need be.
CLI example with ldapsearch
Connect as uid=admin,ou=system and query the LDAP tree ou=users,dc=example,dc=com.
ldapsearch -H ldap:// -D "uid=admin,ou=system" -w apacheds -b "ou=users,dc=example,dc=com"
...
# search result
search: 2
result: 0 Success
# numResponses: 3
# numEntries: 2
Connect with Apache Directory Studio™
Apache Directory Studio™ - The Eclipse-based LDAP browser and directory client
Download Apache Directory Studio from Apache Directory - Downloads
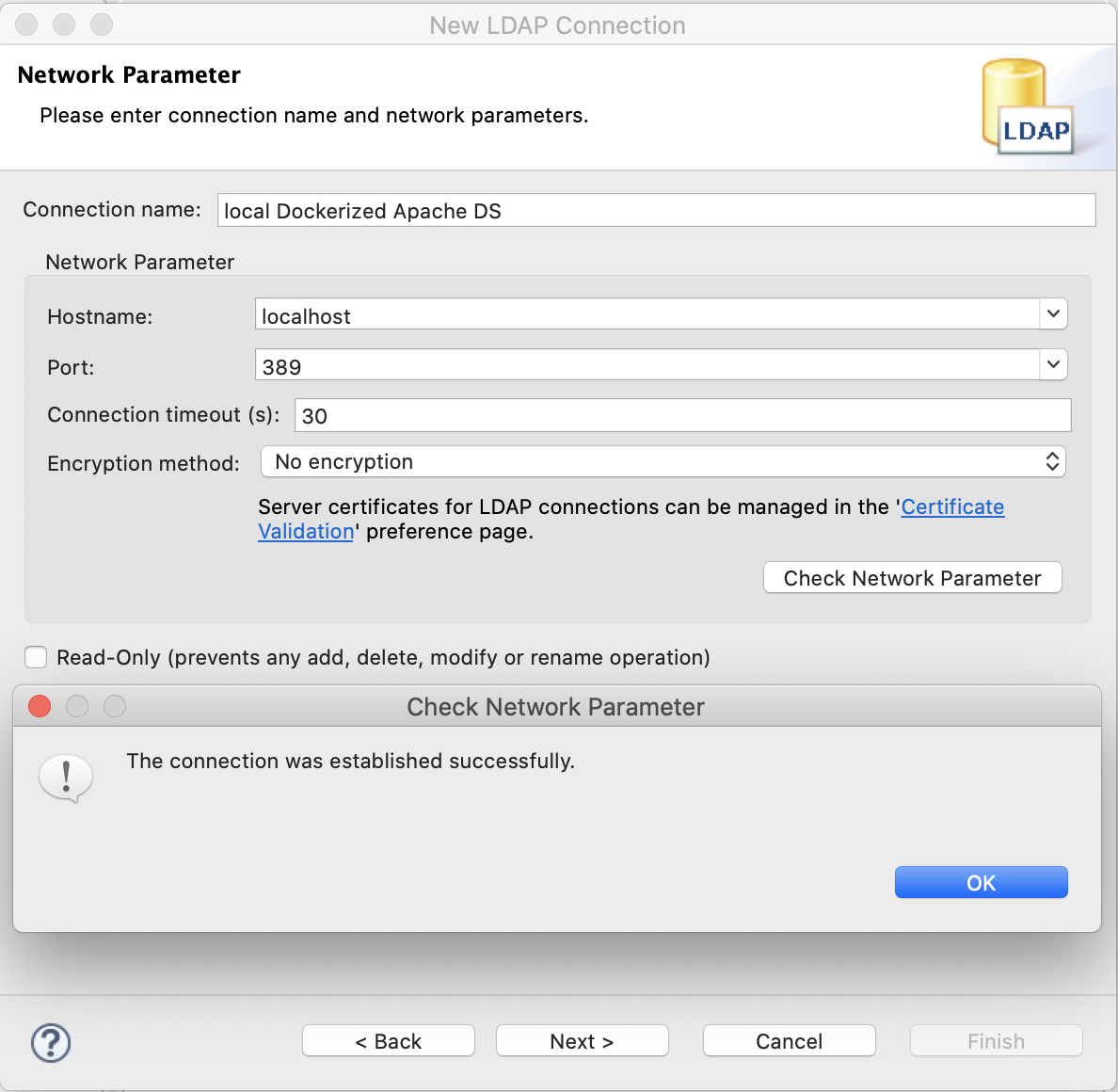
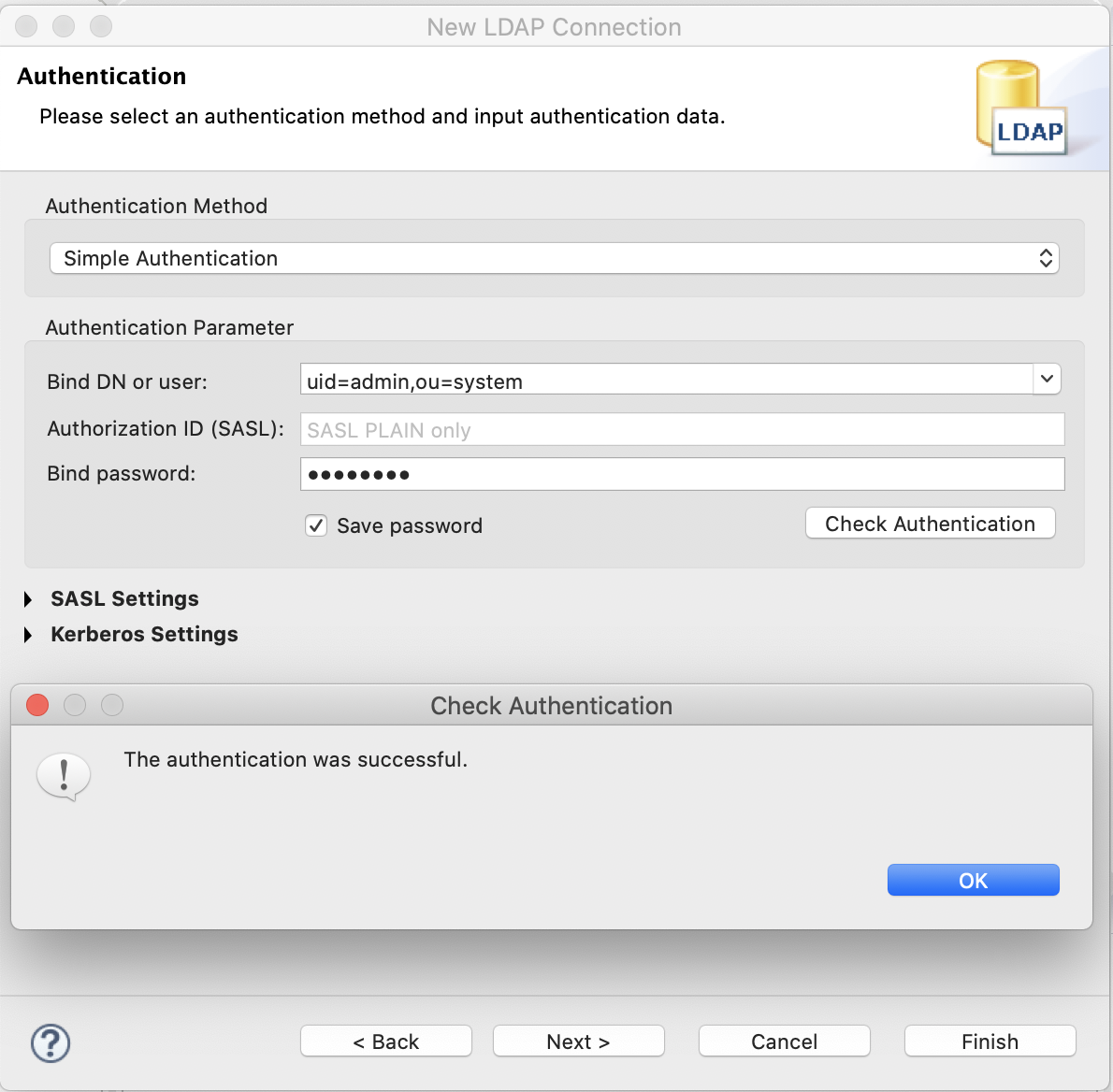
Create (and check) the connection as shown in the screenshots below.
New LDAP Connection - Network Parameter
New LDAP Connection - Authentication
If you made it so far - take the next step and clone the playground datenkollektiv/ldap-playground to get your hands dirty...
Acknowledgment - The docker-compose setup is heavily based on the Docker image provided by TremoloSecurity/apacheds
Photo by Patchanu Noree on Burst